Cryptography sectigostore Cryptography cryptographic hashing signing sectigostore What is a hash function in cryptography? a beginner’s guide
PPT - Swiss army knife in cryptography and information security
Cryptographic hash function Hash function in cryptography: how does it work? Cryptographic hash function
Hash function hashing algorithm cryptography functions explained block minutes types understand complete guide process following illustration
Hash function in cryptography: how does it work?Hashing algorithm algorithms usage okta methodologies Hashing cryptography algorithm input hashed generates hexadecimal thesslstoreCryptographic hash function formally, a hash function can be shown as.
What is a hash function in cryptography? a beginner’s guideIntroduction to hash functions and application of hash functions in Hash cryptographyHash cryptographic cryptography functions function way knife swiss security army information ppt powerpoint presentation resistant.

Hash function in cryptography: how does it work?
Cryptography hexadecimalHash function cryptographic cryptography Cryptography sectigostoreFunction cryptographic formally.
Hash function in cryptography: how does it work?Cryptographic hash function Hash cryptographic function functions introductionHashing algorithm overview: types, methodologies & usage.

Hash cryptographic function cryptography software bitcoin
Hash function cryptographicCryptographic hash functions Hash cryptography function applicationsCryptographic hash function.
Applications and properties of hash function in cryptographyHash functions explained in 2 minutes!! .


Hash Functions Explained In 2 Minutes!! - Society of Robotics & Automation

Introduction to Hash Functions and Application of Hash Functions in

PPT - Swiss army knife in cryptography and information security

Applications and Properties of Hash Function in Cryptography
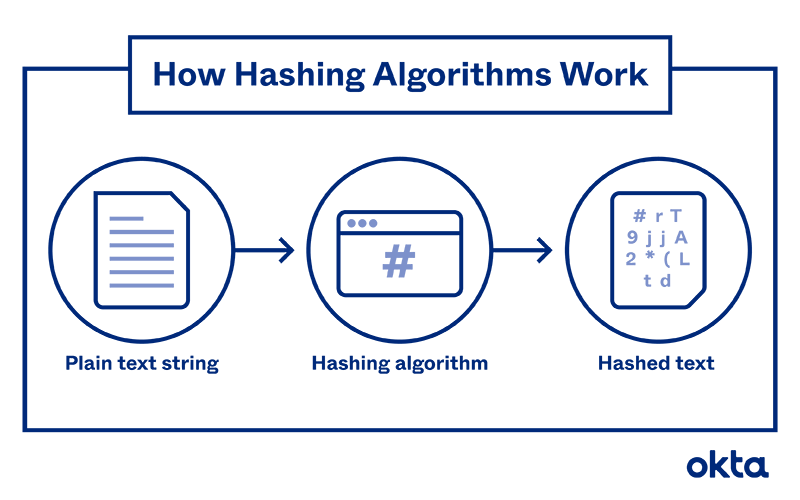
Hashing Algorithm Overview: Types, Methodologies & Usage | Okta

Hash Function in Cryptography: How Does It Work? - InfoSec Insights

Cryptographic hash function - Bitcoin Garden

What Is a Hash Function in Cryptography? A Beginner’s Guide - Hashed

Hash Function in Cryptography: How Does It Work? - InfoSec Insights
